Before I discuss the limitations of any product, I try my best to point out all of the things I appreciate about a product. In general, you will not hear Microsoft tell you about product limitations. I suspect it is a culture thing. But then again, do you expect a new car salesman to tell you about the limitations of the car they are trying to sell you?
So let me first point out that I have been a longtime fan of Microsoft’s Rights Management Services (RMS) which debuted in Windows Server 2003. As the product evolved over the years into what is now called Azure Information Protection, I became an even greater admirer of the product as well as the team within Microsoft responsible for its development.
A key milestone came when RMS was ported to Azure, because it became easy to enable (with one mouse click), eliminating the effort to configure servers on-premises, and especially the underlying Public Key Infrastructure (PKI) environment that RMS required.
With the rise in popularity of Office 365 (100 Million subscribers), many began to take advantage of RMS because it is included for free in the most popular business subscription (known as the “E3” license).
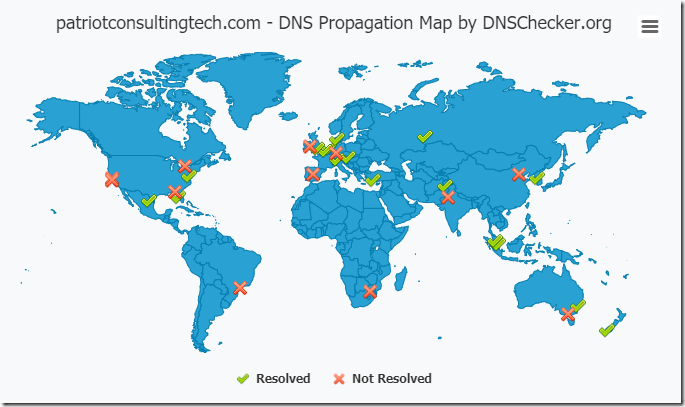
One of my favorite RMS features came in September of 2015, when Microsoft announced Document Tracking and Revocation capabilities (here). I’m still amazed by how cool this feature is, allowing you to see a map of the world and the location of where your documents have been opened!

Another key milestone in the evolution of RMS came when they acquired Secure Islands (announced by Takeshi Numoto on 11/9/2015). Six months later, Dan Plastina (@TheRMSGuy) first announced on 6/22/16 (here) that RMS would be rebranded as “Azure Information Protection” (AIP) and later reached general availability in October 2016 (here).
AIP is a truly jaw-dropping experience. As you are authoring content, the document will automatically be labeled and encrypted with a strong 2048 bit encryption key on-the-fly if sensitive information is found (ex: credit card numbers, social security numbers, or data you define as sensitive using regular expressions).
As a consultant, my job is to listen to customer problems, and then recommend solutions. This leads me to the title of this post – AIP Limitations.
Azure Information Protection Limitations
1. External Sharing using AIP with business partners who are still running Office 2010 (or older) needs improvement
When you protect a document with AIP, and you want to send that document to an external user, things go smoothly if they are running Office 2013 or Office 2016.
However, a lot of companies still run Office 2010. This is what their experience would look like:
“Dear External User,
We would like to share sensitive documents with you. If you are running Office 2013 or 2016, and if you have an Office 365 subscription, then you should be able to open the attachments without a problem.
Otherwise, if you are using Office 2010, you will need the following before you can open the documents we send you:
-
-
- Local Administrator Rights are required to install the Azure Information Protection Client
-
Download and install the Azure Information Protection Client
- If you are running Windows 7, you first need to install KB 2533623 (This will require a reboot)
- Note: Office 2010 require Microsoft Online Services Sign-in Assistant version 7.250.4303.0. This version is included with the AIP client installation, however, if you have a later version of the Sign-in Assistant, uninstall it before you install the Azure Information Protection client.
- Note: The AIP Client will automatically install the .NET 4.6.2 Framework, so be sure not to deploy this on any machine that has known compatibility issues with the 4.6.2 framework.
- Be advised, that in some cases, even if you follow all of the steps above, you may still get an error message when attempting to open an RMS or AIP protected document in Office 2010. The work-around is to create a few registry entries for the service location as documented in the AIP Client Admin guide (here).
If you do not have an Office 365 Subscription, you will need to sign up for “RMS for Individuals” (this is a free identity platform that allows you to open the documents we send to you).”
2. Ad/Hoc External Sharing using an AIP Label is not possible
Let’s say you get a call from a new customer or business partner who wants you to send them a Microsoft Word document. The document is too large to email so you host it in online storage (ex: OneDrive, SharePoint, Dropbox, etc). You might be tempted to click an AIP label that says “Business Partner” or “Client Confidential” but that would not work in the current implementation of AIP, because the Labels must be associated with an RMS Template, and RMS Templates must be associated with Mail Enabled Security Groups, and those Groups must contain a Contact Object. Since normal end-users cannot create contact objects in their Active Directory or Azure Active Directory, they must submit a helpdesk ticket for the external contact to be created, then added to the appropriate Mail Enabled Security Group. You get the picture that this process just broke down fast. Essentially, there is no way with AIP today to associate a label with ad/hoc external sharing. Labels can only be used for defined and known business partners who are pre-configured as contact objects in a group associated with an RMS template that is then tied to a Label. It would be just as exhausting to implement this in a process as it was to type this all out I am sure!
3. There is no Mac OSX client for Azure Information Protection.
The work-around, as best as I can tell, is to have Mac users try the legacy “RMS Sharing App” for Mac OSX. This was the application written before the AIP client was released.
4.In April of 2016, there was a vulnerability discovered in the RMS technology that allows someone with View rights to escalate their privilege and change the document by stripping RMS from the document (which could be potentially undesirable if they then re-share that document with unauthorized parties, or if that document is exposed in the wild (ex: lost/stolen laptop, ransomware, etc). This is documented on Wikipedia here, and proof of concept code is available for testing from GitHub (here). This issue isn’t too great in my opinion, because it requires that one of the named users who is authorized to view the document has to compromise the document. In other words, an unauthorized party cannot break the 2048 bit encryption.
5.OneDrive.
Protecting documents with AIP or RMS automatically when they are uploaded to OneDrive is currently not a great idea. First, Microsoft has removed the navigation button permitting you to do this, so you would have to find the direct hyperlink to the document library settings to enable IRM on your OneDrive document library. Even if you were to do this, it would prevent you from sharing any of those documents with outside users because there is no straight-forward way to make a OneDrive library’s IRM settings understand external users. It essentially ends the ad/hoc sharing capabilities of OneDrive. Perhaps that is why MSFT removed the navigation button for site settings in OneDrive.
Guidance
So given these limitations, what do I recommend?
- I recommend you use AIP to protect sensitive information that should be accessible to internal employees, or known/named individuals from business partners. When communicating with the business partner for the first time, try to find out if they use Office 2010, and if so, warn them that it will be a rocky road for them (see sample email template above). Fortunately, Office 2013 and 2016 seem to natively open AIP encrypted documents.
- If you need to share documents with encryption in transit, then use Office 365 Message Encryption (OME). The limitation of OME (today) is that the recipient can save the document and do anything they want to it (the encryption does not follow the attachments after the recipient saves it to their computer). This will be resolved with the upcoming Secure Email feature that was announced at the 2016 Ignite conference.
- If you need to securely share emails and documents with Gmail users, then wait for the upcoming Secure Email solution that was announced at the 2016 Microsoft ignite conference (watch the video here, starting around the 46 minute mark).
Roadmap
Will things get better? In many cases, yes, however, not for the external user who needs to edit the AIP/RMS protected document using Office 2010.
The proposed Secure Email solution will make it seemless for any user to VIEW AIP/RMS protected documents by providing a web-browser experience. But if the business process requires the external user to make changes and send those back, my understanding is that capability is not going to be in Secure Email when it is released (from what I have heard anyway). To be clear, if the external user is given edit rights, and if they are still on Office 2010, they are going to have the same pain points as I described above with Office 2010.
AIP Licensing
AIP can be licensed in one of four methods:
- You can get AIP as a standalone license for $2/user/month.
- You can get AIP as part of the Azure Active Directory Premium P1 or P2 license families.
- You can get AIP in the Enterprise Mobility + Security E3 or E5 license families.
- Or you can get AIP as part of the Secure Productive Enterprise E3 or E5 license families.
If you just need the original RMS capabilities (encryption, access control and policy enforcement) then you can license that individually or as part of the Office 365 E3 license.
If you need the Document Tracking and Revocation Capabilities, you’ll find that in the Enterprise Mobility + Security E3 or Secure Productive Enterprise E3.
Note: AIP automatic labeling is an advanced feature that requires the AADP P2, or EMS E5, or SPE E5 license. Otherwise, the down-level version of AIP requires the user to manually label documents they create.