Microsoft Defender Advanced Threat Protection (MDATP) is an extended detection and response (XDR) solution, a kind of SHIELD, that combines protection for endpoints (Microsoft Defender ATP), email and productivity tools (Office 365 ATP), identity (Azure ATP), and cloud applications (Microsoft Cloud App Security/MCAS), and many 3rd party solutions like Nextron Systems THOR APT Scanner. As customers face attacks across endpoints, cloud, applications and identities, MTP looks across these domains to understand the entire chain of events, identifies affected assets, like users, endpoints, mailboxes, and applications, and auto-heals them back to a safe state.
Basically, it’s very similar to how S.H.I.E.L.D needs the Avengers to carry out missions. Do you see what I did there? (Thor is an Avenger).
This blog post is about the 3rd party aspect of the XDR when MDATP can tap into THOR to use 12,000 YARA rules from Nextron Systems.
How do you get your hands on YARA rules? Well, you can write your own, but that could take you years to map out all the known threats out there. Or you can purchase a tool like THOR from Nextron Systems, which integrates with their database of 12,000+ YARA rules. The strength of their particular rule set is that it focuses detecting APT threat groups, and over 1,500 web shells. Most EDR systems miss the web shells that these YARA rules detect.
Nextron has previously published their integration capabilities with MDATP on their blog (here) and I highly recommend you check it out.
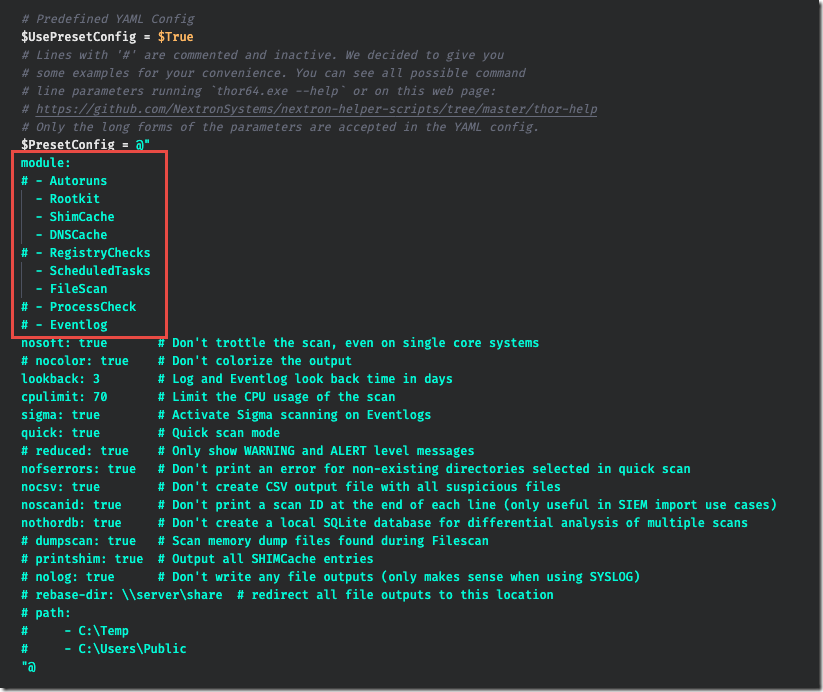
In this blog post, we are going to try out the newest integration from Nextron, which features their THOR Cloud scanner. This was EASY! From start to finish it took me less than 5 minutes. You simply download the PowerShell script from Nextron, which is generated to include the license key, upload that script into MDATP’s Live Response, and in less than one minute, get a report back on any matches that were found from the THOR scan. The default configuration, quick scan, can be modified to include additional modules such as Registry and Process, but this will increase the scan time from 1 minute to ~15 to 20 minutes. A scan of the entire file system and event log could extend the time to 40 minutes to 3 hours depending on the number of files and types of contents. I recommend getting started with quick scan first so you can see how it works. If you decide to make changes, here is a screen shot of the section of the script you can change:
Step 1. Obtain a license key from Nextron.
Note: This blog post will be updated with more details about an upcoming webinar in June, 2020 featuring Florian Roth (@cyb3rops)
Step 2. Launch MDATP Live Response Session
Note: As of April 6th, Live Response now runs on Windows 10 1709 or newer (it was previously only available on 1903 or newer). Make sure you have Live Response and Custom Scripts enabled in MDATP (they are off by default). You’ll need to enable, at least, the minimum Remediation Level for a given Machine Group.
Upload the thor-seed.ps1 file that you obtained from Nextron.
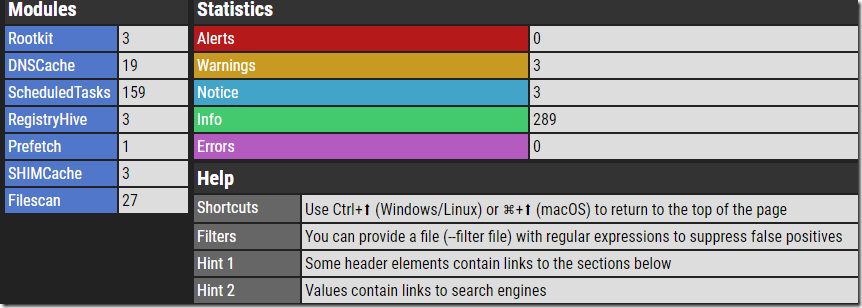
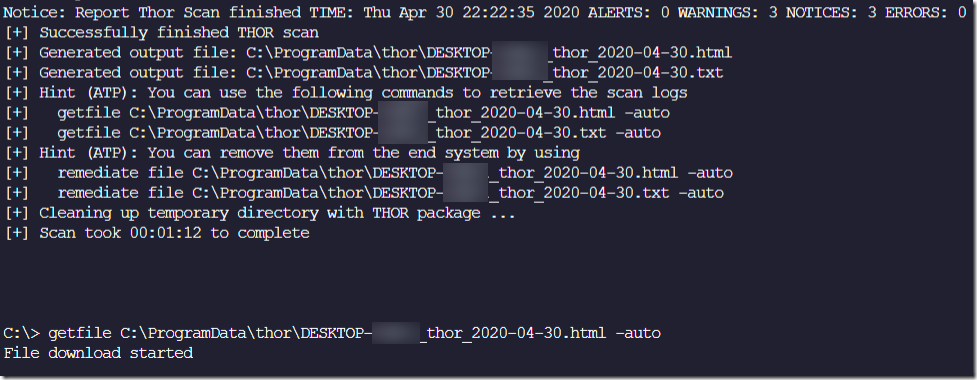
The scan completed in just under one minute. Very fast, when you consider it used over 12,293 YARA rules!
It produced a handsome HTML report in C:\ProgramData\thor
I first ran this on a clean system to create a baseline, I wanted to make sure I didn’t get too many false positives on a machine I expected to be clean. It was very accurate, because it detected TOR but no other false indicators.
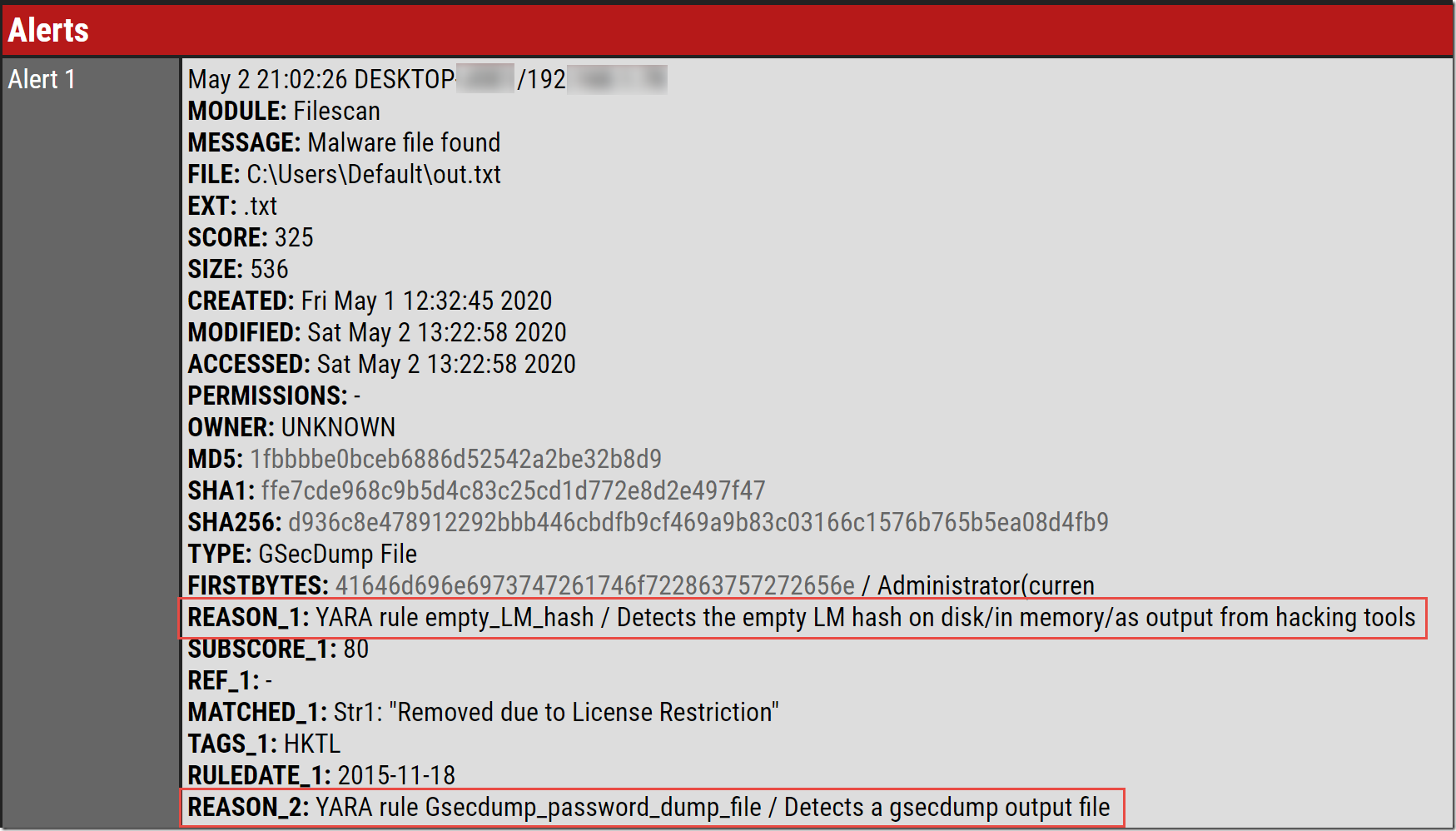
On another system I tried, it reported a file containing dumped password hashes, created from Gsecdump (developed by Johannes Gumbel).
Here is an example of PSEXEC.exe being found even though it was renamed to 2.exe
After the scan completes, it provides hints on the syntax to remotely retrieve the HTML report and detailed TXT files from the remote system, and then remove them with the remediate command.
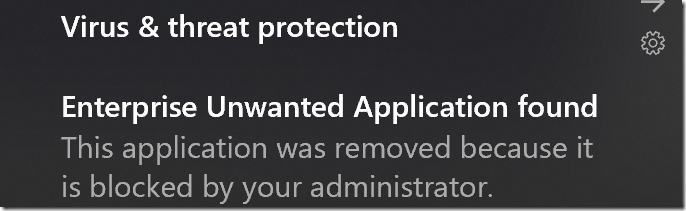
If you run the scan twice, you need to first remove the prior HTML and TXT files. If you use the Remediate command, it will create a pop-up on the target machine that the file was removed.
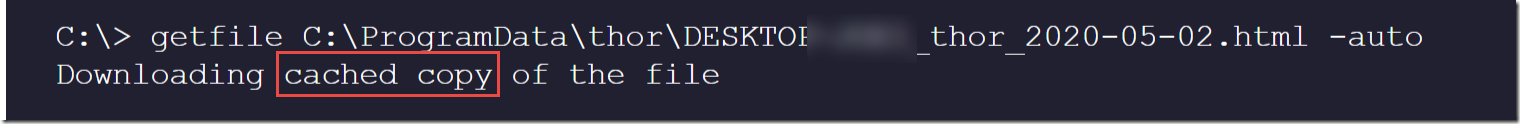
Another interesting lesson I learned is that even if you delete the HTML report, if you download it a second time, Defender will still grab a cached copy from the first download
I believe adding the timestamp to the file name should eliminate this cache problem.
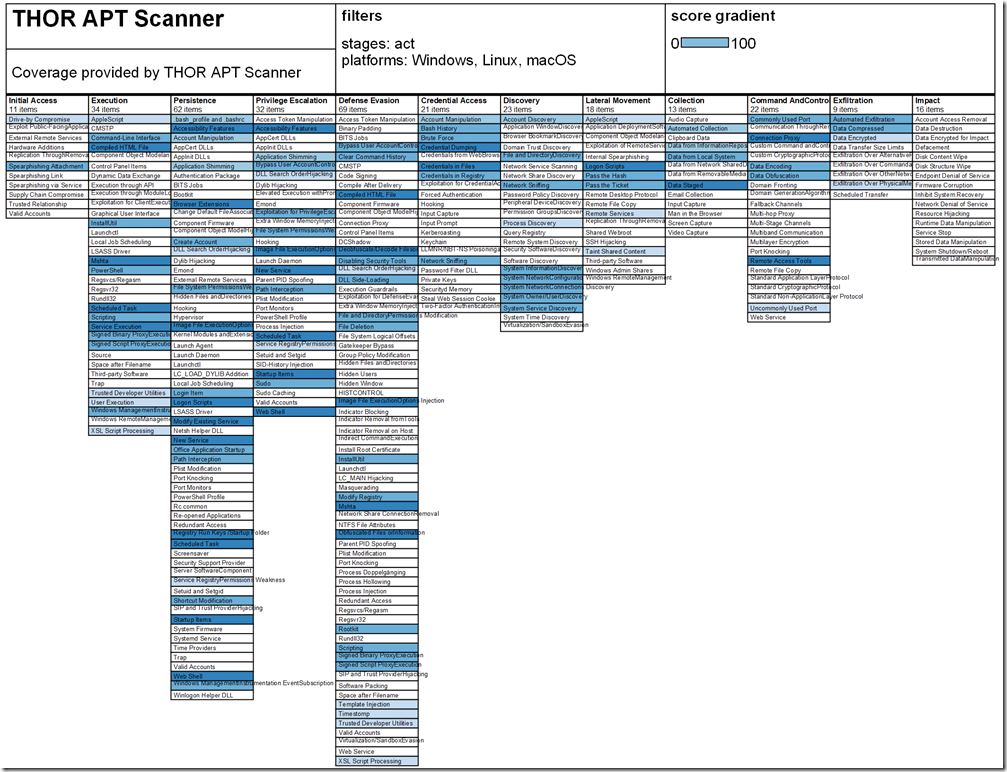
Overall, I would highly recommend this whenever you are investigating a threat with MDATP because many of these YARA rules detect threats that are not yet found in VirusTotal. These YARA rules from Nextron effectively extend the MDATP detection capabilities as shown below. For example, the presence of TOR.exe, PSEXEC.exe, or the LM Hash dump from Gsecdump were not flagged as alerts inside MDATP EDR.
Also, check out the latest MITRE evaluation of MDATP against the Russian Hacking Group “Fuzzy Bear” aka APT 29 (here).