Did you know that 91% of successful data breaches started with a spear-phishing attack? (According to research from Trend Micro).
Two of my customers have informed me that their top executives’ email have been ‘spoofed’ by hackers. I have included the message headers from those spoofed emails in the blog post below (scrubbing the names to protect the innocent).
The hackers are exploiting a weakness in the Simple Mail Transport Protocol (SMTP) to masquerade themselves as a top executive, who then send an urgent email to staff to click a hyperlink or open an attachment. You can imagine what happens next: the computers get infected by Ransomware like CryptoLocker, encrypting not only hard drives, but also entire departmental file shares. Check your backups – this may be your only option to recover data that has been encrypted. The latest variants of ransomware are now trying to erase network connected backup storage too – so be extra vigilant to keep an offline copy of your backups.
So when my customers asked me what they can do to prevent email spoofing, I asked for a copy of the message headers that the attackers used and found out that the emails were getting through despite failing Sender Policy Framework (SPF) checks. SPF checks are the most common method to combat email spoofing. In this article I will describe how DMARC can better enforce your SPF record values to prevent spoofed email from passing through. I recently did a survey of 200 companies and found that only 12% have implemented DMARC so far.
SPF is implemented by creating a type of DNS record called a ‘TXT’ that contains an authorized list of senders for that particular email domain. However, many companies have not implemented the most hardened syntax for the SPF record, known as the hard fail “-all.” Instead, they are implementing the soft fail “~all.” This allows for emails that do not match the authorized list of servers to pass through, albeit with a higher spam confidence level (SCL) score.
Up until recently, it seemed as if SPF was all that was required to cause email filters to adjust the SCL high enough to cause spoofed emails to go into a quarantine or junk mail folder. All that started to change when the attackers started to use valid email servers hosted by trusted email providers such as GoDaddy. This caused the SCL score to be low enough for the email to pass through as legitimate “enough” to look like a standard email.
Additionally, and probably more significantly, hackers are now spoofing the RFC 5322.From header which cannot be detected by an SPF check. SPF is great for protecting against attacks where the 5321.MailFrom header is spoofed. Where SPF has problems is when the 5322.From header (the address that you see in Outlook).
Scroll down to see the (scrubbed) message headers in detail.
How do we stop spoofed emails?
Enter DMARC, which stands for “Domain-based Message Authentication, Reporting & Conformance”, is an email authentication protocol. It builds on the widely deployed SPF and DKIM protocols, and was submitted as RFC 7489 on March 18th 2015.
In a nutshell, DMARC is another type of DNS TXT record that builds on SPF and DKIM records and can be configured to specifically tells email filters to reject emails that did not originate from the senders authorized from the SPF or DKIM records. This is enough to stop spoofed emails cold in their tracks. Here is an example of a DMARC record:
v=DMARC1; p=quarantine; rua=mailto:[email protected]
What this does is to send items to quarantine if the SPF record or DKIM checks fail, and to send reports to an email address that you specify.
Prior to implementing a DNS record type for DMARC, it is important to talk to your marketing department for a list of companies that they send emails through, for example MailChimp. Those services must be in the SPF record otherwise they will be rejected. After the SPF has been updated, the hardfail setting should be changed to “-all” and the DMARC setting should be configured to reject. Organizations that aren’t sure which services their marketing companies are using can enable DMARC in monitoring mode so that they can first learn who is sending emails out.
To test out your email system, you can send emails to these addresses and get a report back:
1. If you wish to receive the results at the address in the “mail_from,” the sample message should be sent to [email protected].
2. If you wish to receive the results at the address in the “from” header, the sample message should be sent to [email protected].
Disclaimer: All content provided is for informational purposes only. Use at your own risk.
Message Header Analysis
Take a look at these two spoofed message header (names have been changed to protect the innocent):
First Example – Spoofed email originating from GoDaddy
Authentication-Results: spf=permerror (sender IP is 184.168.200.142)
smtp.mailfrom=contoso.com; contoso.com; dkim=none (message not signed)
header.d=none;contoso.com; dmarc=none action=none header.from=contoso.com;
Received-SPF: PermError (protection.outlook.com: domain of contoso.com used an
invalid SPF mechanism)
(envelope-from <[email protected]>)
From: (Real CEO’s Full Name) [email protected] <– RFC 5322.From
To: (Unsuspecting End-User – Probably in Accounting Department) <[email protected]>
Subject: Let Me Know Asap!!
Reply-To: <[email protected]> (Attacker’s address, or unsuspecting innocent 3rd party)
Mail-Reply-To: [email protected] (Attacker’s address, or unsuspecting innocent 3rd party)
X-Sender: [email protected]
X-AntiAbuse: Primary Hostname – p3plcpnl0222.prod.phx3.secureserver.net
X-AntiAbuse: Original Domain – contoso.com
X-AntiAbuse: Sender Address Domain – contoso.com
X-Get-Message-Sender-Via: p3plcpnl0222.prod.phx3.secureserver.net: authenticated_id: noreply@(LegitimateEmailDomainAtGoDaddy)
Return-Path: [email protected]
Second Example – Spoofed email originating from POBOX.com
Return-Path: <[email protected]>
X-Env-Sender: [email protected]
X-SpamWhitelisted: domain whitelist
X-StarScan-Version: 8.11; banners=contoso.com,-,contoso.com
X-VirusChecked: Checked
Received: (qmail 121067 invoked from network); 21 Mar 2016 16:38:30 -0000
Received: from pb-sasl-trial1.pobox.com (HELO pb-sasl-trial1.pobox.com)
DHE-RSA-AES256-GCM-SHA384 encrypted SMTP; 21 Mar 2016 16:38:30 -0000
Received: from pb-sasl-trial1.pobox.com (localhost [127.0.0.1]) by
pb-sasl-trial1.pobox.com (Postfix) with ESMTP id 8D0A21017B for
<[email protected]>; Mon, 21 Mar 2016 12:38:30 -0400 (EDT)
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed; d=pobox.com; h=mime-version
:content-type:content-transfer-encoding:date:from:to:subject
Received: from pb-wm-sasl1.int.icgroup.com (pb-wm-sasl1.int.icgroup.com
[10.80.80.58]) by pb-sasl-trial1.pobox.com (Postfix) with ESMTP id 7F0521017A
for <[email protected]>; Mon, 21 Mar 2016 12:38:30 -0400 (EDT)
Received: from webmail.pobox.com (unknown [10.80.80.19]) (using TLSv1.2 with
cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)) (No client certificate
requested) by pb-wm-sasl1.pobox.com (Postfix) with ESMTPSA id 0A27539EC9 for
<[email protected]>; Mon, 21 Mar 2016 12:38:30 -0400 (EDT)
Date: Mon, 21 Mar 2016 17:38:29 +0100
From: Real CEO’s Full Name [email protected] <– RFC 5322.From
To: <[email protected]>
Subject: Invoice Payment
Reply-To: <[email protected]> (Attacker’s address, or unsuspecting innocent 3rd party)
Mail-Reply-To: [email protected] (Attacker’s address, or unsuspecting innocent 3rd party)
X-Sender: [email protected]
User-Agent: Roundcube Webmail/1.1.1
X-Pobox-Relay-ID: 57FC50A6-EF83-11E5-B2BA-E24DCCAB2AED-19029152!pb-wm-sasl1.int.icgroup.com.pobox.com
X-MS-Exchange-Organization-AuthSource: RealExchangeServerHostName.contoso.com
X-MS-Exchange-Organization-AuthAs: Anonymous
And here is how authentic the email would look to the recipient:
—–Original Message—–
From: Real CEO’s Full Name [mailto:[email protected]]
Sent: Monday, March 21, 2016 9:53 AM
To: (Unsuspecting End-User – Probably in Accounting Department) <[email protected]>
Subject: RE: Invoice Payment
Jane,
I need you to process an urgent payment, which needs to go out today as a same value day payment. Let me know when you are set to proceed, so i can have the account information forwarded to you once received.
Awaiting your response.
Regards
Thanks.
–
Sent from my iPad
I am in the office today.
—–End Original Message—–
O365 and DMARC
Because SPF fails, and because DKIM can fail, and because this is all due to routing, EOP will not enforce DMARC failures if your primary MX does not point to EOP. EOP can still detect if a message passes DMARC when the DKIM-signature passes.
https://blogs.msdn.microsoft.com/tzink/2014/12/03/using-dmarc-in-office-365/
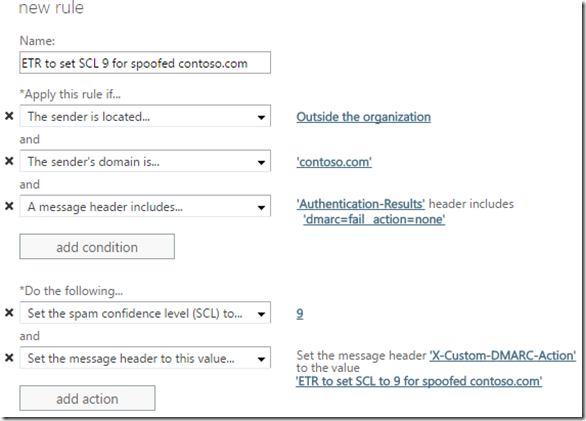
For Office 365 customers, if you do not set the DMARC value to p=reject, then it is recommended to create a message transport rule to set the spam confidence level to 9 so that it doesn’t hit the user’s inbox. The advantage of this is that your domain cannot be spoofed by outside senders for inbound messages to your organization which is common in spear phishing, yet marketing messages that go over the Internet are not affected.
Summary
In the first example, the email passed through the Exchange Online Protection filters. In the second example, the email was passed through MessageLabs filters. In the second example, since there was no hyperlink or attachment, we can only assume that the reply TO address was the attacker’s actual email address. Whereas in the first example, the reply TO address was forged because the attacker only wanted the recipient to click on a hyperlink.
After implementing DMARC, the message header section “Authentication-Results” will contain instructions to reject both of these emails.
Dmarc relies upon SPF *or* DKIM. So if you can’t do outbound DKIM signing, you can still enforce DMARC on an SPF hard fail to prevent inbound mail from coming through as spoofed.
Advanced Threat Protection from compromised Vendors
DMARC provides an excellent layer of defense to add to your defense in depth security policy, preventing spoofed mails from reaching your internal users. For situations where an attacker is not spoofing your domain, but is instead spoofing one of your trusted Vendors domains, DMARC would have to be implemented by your Vendor before it would protect you. In the trusted Vendor scenario, you can best protect yourself by adding an advanced layer of protection to scan for phishing hyperlinks and zero-day vulnerabilities that are not yet in virus definition files. One such solution is Microsoft Advanced Threat Protection (ATP). ATP will detonate attachments in a cloud-hosted virtual machine and observe it for malicious intent before delivering it to your end-users. It will also replace Hyperlinks with ‘safe links’ which are scanned at the time the user clicks on the hyperlink. For more information on Advanced Threat Protection, or to schedule a free consultation to have Patriot Consulting configure it in your Office 365 tenant free-of-charge, contact us at [email protected].
References
Demarc Deployment Tools, Generators and Checks: ttps://dmarc.org/resources/deployment-tools/
For more information on DMARC, check out www.dmarc.org
www.dmarc.org
https://dmarc.org/wiki/FAQ#How_does_DMARC_work.2C_briefly.2C_and_in_non-technical_terms.3F
https://blogs.technet.microsoft.com/eopfieldnotes/2015/02/26/using-dmarc-to-prevent-spoofing/
https://blogs.msdn.microsoft.com/tzink/2014/12/03/using-dmarc-in-office-365/
https://blogs.msdn.microsoft.com/tzink/2015/03/03/best-practices-for-exchange-online-protection-customers-to-align-with-dmarc/
https://blogs.msdn.microsoft.com/tzink/2015/03/13/how-to-align-with-spf-and-dmarc-for-your-domain-if-you-use-a-lot-of-3rd-parties-to-send-email-as-you/