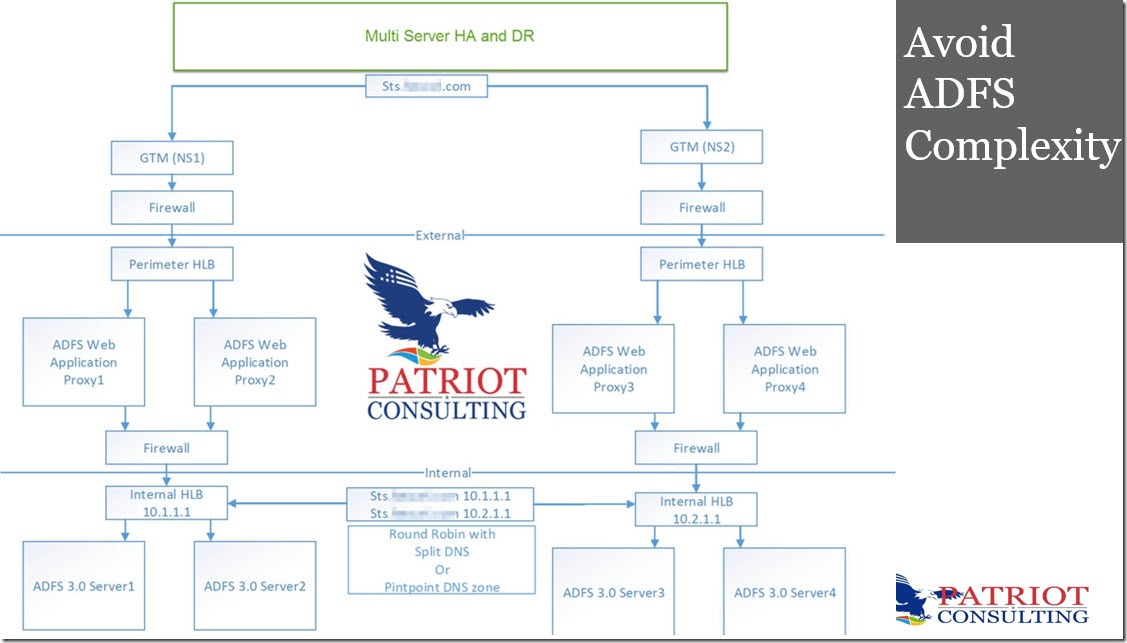
A surprising number of clients are still operating complex ADFS farms.
Here are 8 reasons to switch to Azure AD.
1. ADFS has a greater surface attack area than Azure AD. Example: NTLM Brute-Force (CVE-2019-1126).
2. ADFS can have multiple single points of failure unless designed properly
3. ADFS requires certificate maintenance – resulting in planned downtime
4. ADFS requires lots of IT overhead (Backups, Monitoring, OS Upgrades, etc)
5. Azure AD Conditional Access offers better security controls than ADFS Claims
6. Azure AD is lightweight and less complex to administer (No Claims Rules)
7. Azure AD more closely aligns to NIST 800-63b (Scan for breached passwords)
8. Azure AD has a better feature roadmap
It’s easy to switch from ADFS to Azure AD. For example, this one PowerShell command can migrate Office 365 from ADFS to Cloud in less than 5 minutes. Set-MsolDomainAuthentication -DomainName mydomain.com -Authentication Managed
You can also do a staged rollout of smaller groups at a time rather than a big bang cutover using (the first security group is limited to 200 users). Learn more about staged rollout (here).
Note: That’s the core command that moves the trust from ADFS to Azure AD. There are more planning steps involved like making sure you have enabled password hash sync. Learn more planning steps (here).
Here are 5 tips for moving other apps from ADFS to Azure AD
- Use the new ADFS Application activity report (preview) or the ADFS to Azure AD app migration tool to analyze your current apps. This tool will quickly identify which apps can be migrated seamlessly and which require remediation (see figure one).
- Acquire deployment guides for the relevant apps. Many are published on the Microsoft app gallery, but if not, you can open a ticket through the third-party vendor who developed the app.
- Allocate appropriate time and resources to the high-touch apps.
- Migrate the apps that are ready to go for quick wins.
- Identify a test environment or plan a maintenance window to avoid moving large servicing app at peak usage.
Learn more here: