According to the latest Microsoft Security Intelligence Report, spear phishing remains the preferred attack method used by hackers. Microsoft detected a 250% increase in phishing messages between January and December 2018.
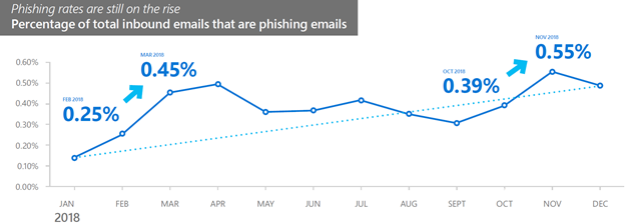
Figure 1 Page 21 of the Microsoft Security Intelligence Report Volume 24
Many organizations have deployed 2FA as a layer of defense to guard against phishing, so that if the user gives away the username and password, the attacker shouldn’t be able to logon to the user account. The purpose of this blog post is to raise awareness that Office 365 in particular is now vulnerable to “network session hijacking proxy theft” which allows an attacker to sign in regardless of the MFA solution (MSFT, Duo, RSA, SMS, etc). The authentication token is captured after the victim is tricked to going to a credential stealing website where they perform MFA through a proxy server. The token is then re-played by the attacker who can sign in as the user.
To see a demonstration of this, watch this Youtube video,
Kuba Gretzky – Phishing Through Modern 2FA Defences With Evilginx – YouTube
The cookie import was done using EditThisCookie
Prior to this video, I haven’t been able to find any evidence of blog posts or videos demonstrating a successful bypass against Office 365’s 2FA capabilities. It’s worth noting that Office 365 is not unique – the same man-in-the-middle attack works against Google, LinkedIN, and other platforms as first demonstrated by Kevin Mitnick (KnowBe4) in May 2018 (original blog post (here). Since then other phishlets have been developed for Amazon, Github, Protonmail, Citrix, OKTA, Twitter, Instagram, Facebook, reddit, and consumer Outlook.com, and now Office 365.
The reason why this is important is because much of the security industry emphasizes MFA without raising awareness of this man-in-the-middle threat. For example, in my opinion one of the best presentations at the 2018 RSA conference was given by Booz | Allen | Hamilton which gave overwhelming evidence that 2FA would have stopped or reduced the impact of every one of the 159,700 total cyber incidents reported by the Online Threat Alliance in 2017. (Page 6, reference here). Now, the caveat has to be added that MFA would have stopped cyber incidents as long as victims were not tricked to going to proxy websites.
We have taken for granted that the very best anti-spam/anti-phish security solutions will not block 100% of the threats, and it is now time we accept the reality that MFA will not always prevent unauthorized authentication (much like how the SMS version of 2FA is no longer recommended or sufficient).
Roger Grimes of KnowBe4 gave a wildly popular presentation at the 2019 RSA Security Conference (requiring overflow seating) which listed 12 methods to bypass MFA (PDF download here). Some of these techniques require the attacker to invest a lot of time and sometimes money and risk (sim swapping) or be adept at social engineering (phone number porting). However, this all changed when Kuba Gretzky (@mrgretzky) released EvilGinx in 2017. Kuba showed how attackers can reduce their risk, cost, and effort through “network session hijacking proxy theft.” Grimes mentioned this technique among the 12 MFA bypass methods in his RSA presentation, and included a video showing how Kuba’s updated EvilGinx2, successfully bypasses the 2FA of Gmail and LinkedIN. At that time, there was no Office 365 phishlet available, but it was later added by @JamesCullum.
In January at a Microsoft event, I asked Microsoft if Office 365 defended or detected network session hijacking proxy theft, specifically EvilGinx2. They stated that Office 365 would prevent this technique. [See part two of this blog series to see how]
Enter Aidan Holland (@thehappydinoa), who recently verified that EvilGinx2 can successfully bypass Office 365’s 2FA. Aidan also solved a vexing problem for Troy Hunt, who was trying to get a list of the Fortune 500 for his security research. Read about his solution to solve that problem here.
It’s worth noting that the phishing link generated by EvilGinx2 is not blocked by MSFT EOP, Office ATP, Microsoft Defender ATP, or Windows Defender SmartScreen.
In the next blog post (here), I will discuss ways to protect against EvilGinx2.
