Immediately after installing Skype for Business Server 2015 (Standard Edition) the front-end services would not start.
Tom Rimala’s blog article that suggested there is a problem when the internal Certificate Authority uses MD5 as the signature signing method.
Also, the Microsoft Certificate Requirements says “The default digest, or hash signing, algorithm is RSA.” (no mention of MD5).
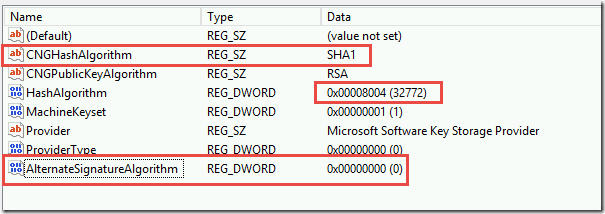
I changed the CA Authority’s certificate from MD5 to SHA1. Here is the registry key to change on the Root CA signing information (we changed these three values). Note: the guidance was to change this on the Root and Subordinate but in our case the Root was also the issuing CA, so there was no subordinate to change in our case.
The next step is to restart the Root CA services. Then issue a new Root Certificate. Then copy the new root CA cert to the Skype for Business front-end, and finally re-issued the Front End Cert and OATH cert. Then the services should start up.
There was a false negative warning about Event ID 32174 “Server startup is being delayed because fabric pool manager has not finished initial placement of users.” This is clearly a bogus error because a Front-End server doesn’t have additional servers to place users into.
There was a clue about the Certificate problem because the System Event log contained a ton of Schannel events such as 36888, “A fatal alert was generated and sent to the remote endpoint. This may result in termination of the connection. The TLS protocol defined fatal error code is 40. The Windows SChannel error state is 1205.” And Event ID 36874 “An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.” I am adding these details in the event that a search engine might index these errors to point people to this fix.