In this three-part blog series, I will be writing about interesting trends amongst the Fortune 500 using public DNS reconnaissance posted in open source github repositories. This first post is focused on the email security providers used by the Fortune 500. The other posts will analyze adoption trends in DMARC and IdP Federation.
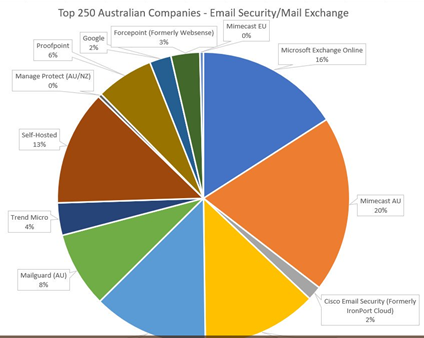
One of the favorite people I follow on twitter is Daniel Streefkerk (@dstreefkerk) from Sydney, Australia. Daniel tweeted on February 11th about a script he published to github (here) that performs DNS reconnaissance He posted a graph (here) of which email security providers were used by the top 250 Australian Companies.
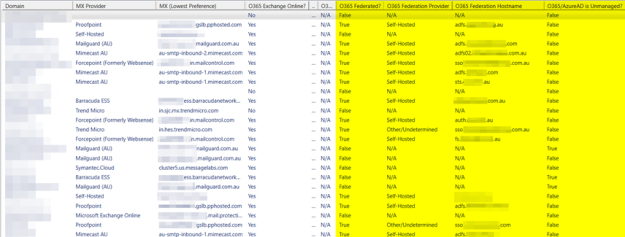
Then a few days later he posted (here) how he updated the script to check for federation information (ex: Does the domain federate with OKTA, ADFS, Ping, OneLogin, etc?) and other interesting things like whether Office 365 was detected, the tenant name discovered (typically it is publicly listed in the DKIM DNS record).
I was curious how his findings in Australia compared to companies in the United States, but I couldn’t think of a simple way of finding the fortune 500 email domain names. Turns out, I was not alone. One of Daniel’s fellow Auzzies, Troy Hunt, a Microsoft Regional Director (a title similar to an MVP) recently asked a similar question (here) on March 31st:

Everyone seemed to have ideas but Troy seemed frustrated at one point that there wasn’t a simple list available somewhere. That’s when Aidan Holland (@thehappydinoa) came to the rescue and wrote an elegant 152-line python script (here) to gather about 455 of the 500 from a JSON query against hifld data. He then took that data and queried virus total, threat crowd, crt.sh, and finally validated it was a valid DNS domain for email by querying the MX record in DNS. All in 152 lines of Python. Impressive.
His JSON query the initial data set came from ARCGIS.COM with this code:
FORTUNE_500_JSON
=
“https://opendata.arcgis.com/datasets/a4d813c396934fc09d0b801a0c491852_0.geojson”

Aidan published the resulting list of 455 domain names (here). Then using PowerShell, we can pipe that into Daniel’s DNS recon script, to produce a report showing the email filtering systems used by the Fortune 500.
Get-Content fortune_455_emails.txt | .\Invoke-EmailRecon.ps1 | Export-Csv 455.csv

Raw Table Results:
|
Email Security Vendor |
Count |
|
Proofpoint |
141 |
|
Self-Hosted |
91 |
|
Microsoft Exchange Online Protection (EOP) |
83 |
|
Other/Undetermined |
59 |
|
Symantec.Cloud |
36 |
|
Cisco Email Security (Formerly IronPort Cloud) |
27 |
|
|
11 |
|
Forcepoint (Formerly Websense) |
4 |
|
Trend Micro |
2 |
|
FireEye Email Security Cloud |
1 |
The results indicate that most are using ProofPoint, Exchange Online Protection, or they are self-hosting their own service of some type.
Comparing the results to Australia, we can see that the US Market is consolidated to a few big players, whereas Australia is reasonably diversified. The significance of this is that malware should theoretically spread slower in Australia, because malware authors would have to work significantly harder to find vulnerabilities across multiple email security solutions if they wanted to infect the majority of the top 250 companies in Australia, whereas in the USA the malware authors just need to find a flaw in ProofPoint and Exchange Online Protection to infect 50% of America’s Fortune 500.
What surprised me was to see ProofPoint has a 6% penetration into the Australian market, compared to 28% in the United States (no surprise since ProofPoint HQ is in the USA).
These results could also be helpful for smaller or mid-size businesses who sometimes look at the decisions made by members of the Fortune 500 as a standard, ex: “good enough for them, good enough for me.”
Universities, think tanks, and research firms like Gartner and Forrester can now take periodic snapshots of this data to determine trends of email security vendors (or IdP federation vendors). Companies could use this data to find out which markets to expand into. And unfortunately Malware authors have most likely already figured out that targeting flaws in ProofPoint and Exchange Online will net them 50% of the Fortune 500.
In the next blog post, I will examine DMARC and IdP adoption trends.
