On September 10th, 2019, Microsoft released Azure AD Connect v1.4.
Customers that had configured their Azure AD Connect for auto-upgrade are now experiencing rolling upgrades, which can cause mass deletion of devices from Azure AD. One of my clients contacted me today after receiving a rather alarming and unsettling email about several hundred objects being deleted:
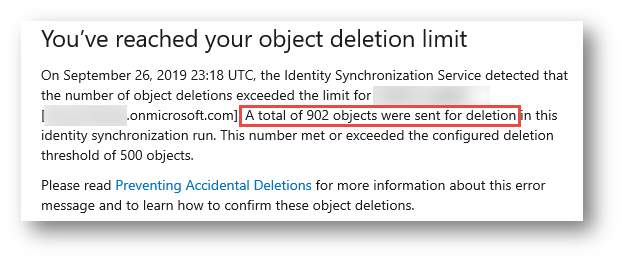
Their question to me was: “This is very concerning. Should I be worried or no?”
My immediate response was “Call me ASAP!” – as I thought that someone had restructured their organizational units in Active Directory, which is a common cause of mass deletion of objects from Azure AD. As I waited for the remote sharing invite to arrive in m y inbox, I began formulating my plan: identify the OU that changed, go into AAD Connect and start syncing that OU again, and then on next full sync, it would restore all the soft deleted objects. I’ve done this before, so I was expecting to bring this issue to closure quickly… or so I thought.
After further investigation, we couldn’t find any evidence of OU changes. In fact, this customer followed best practice by not performing OU filtering (which avoids the problem of OU changes causing mass deletes).
Puzzled, I noticed that in the AAD Synchronization Service, the first instance of the mass delete event occurred as part of a FULL Sync. “Aha!” – I thought to myself, a full sync can only occur when a human is involved, so let’s track down who did this and have a chat. If left unprovoked, AAD Connect only runs Delta syncs every 30 minutes.
We quickly ruled out human involvement, as there was no evidence of any recent interactive logon.
The next thought that came to mind was a feature of AD Connect, called Auto Upgrade. We checked the Control Panel > Programs and noticed that AAD Connect was updated today. Aha! .. But why would the upgrade cause a mass deletion?
We then looked at the Azure AD release notes and noticed this explanation:
With this version of Azure AD Connect some customers may see some or all of their Windows devices disappear from Azure AD. This is not a cause for concern, as these device identities are not used by Azure AD during conditional access authorization. For more information see Understanding Azure AD Connect 1.4.xx.x device disappearnce
Then scrolling down to the Fixed Issues section we saw:
“Fixed a bug where non-Windows 10 computers were syncing unexpectedly. Note that the effect of this change is that non-Windows-10 computers that were previously synced will now be deleted. This does not affect any features as the sync of Windows computers is only used for Hybrid Azure AD domain join, which only works for Windows-10 devices.”
Fascinating. So this explained why we saw 900 objects attempt to be deleted, and upon verification, they were Windows 7 objects, and Windows Server objects.
SURPRISE…
Azure AD Connect will not permit more than 500 objects to be deleted, so that is why the warning email was sent. We surmised that the proper thing to do was to remove the deletion protection mechanism otherwise the AAD Connect would perpetually remain in an error-status, unable to delete all these devices itself.
So we ran these three PowerShell Commands on the AAD Connect Server:
Disable-ADSyncExportDeletionThreshold
Then we started a full sync:
start-adsyncsynccycle -policytype Initial
Then after watching the deletion finish in the Synchronization Service GUI tool, we re-enabled the deletion threshold:
Enable-ADSyncExportDeletionThreshold -DeletionThreshold 500.
Hopefully this helps! More information about this issue can be found here:
